Alert
Introducing WolfPAC’s New Manage Controls Functionality
We’re excited to unveil a complete overhaul of the WolfPAC platform’s Manage Controls functionality that...
6,000+ users trust WolfPAC Integrated Risk Management software to protect and plan for their future.
We partner with you to identify and address your specific risks and needs, providing you with next-generation solutions to manage the evolving risk landscape
Find Out More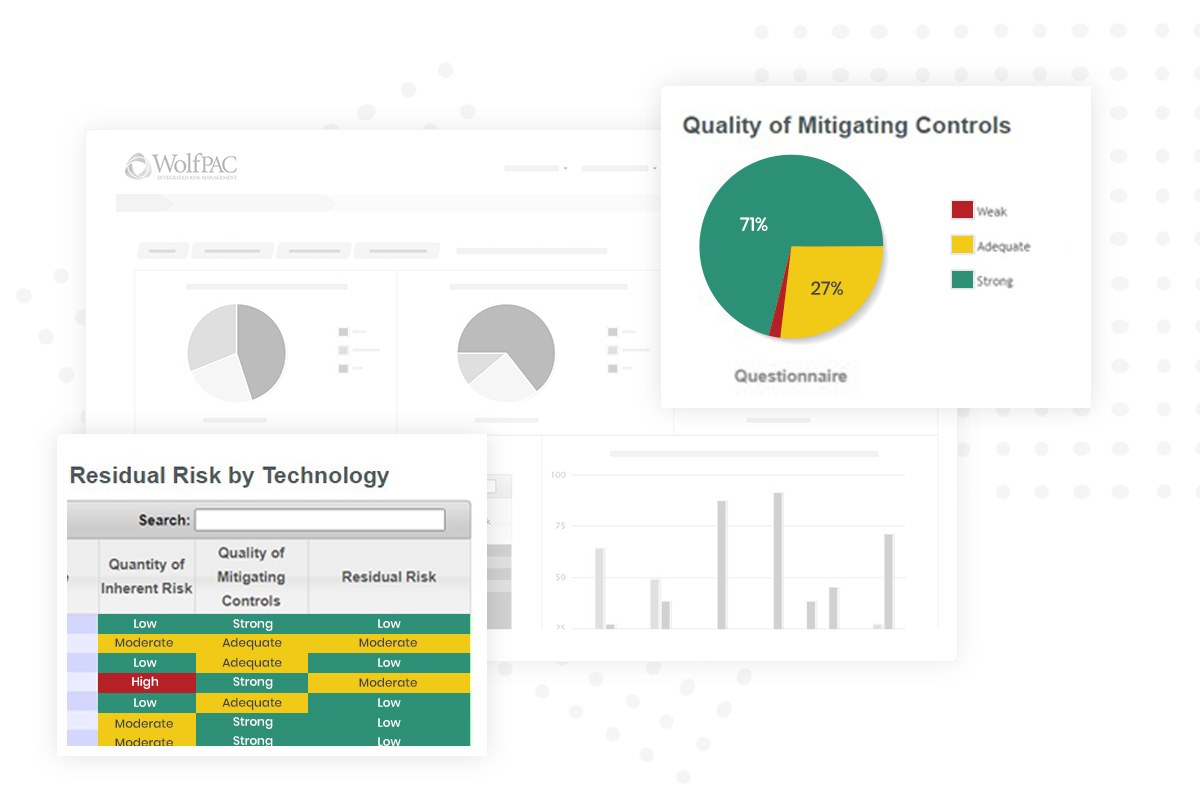
Our holistic software solutions deliver a comprehensive view of your risk data, bolstering your security and minimizing business interruptions
Find Out More
Our team is ready to help you succeed, whether you choose to drive your own software deployment or receive expert assistance and training
Find Out MoreWolfPAC gives your organization everything you need to manage risks and reach your goals